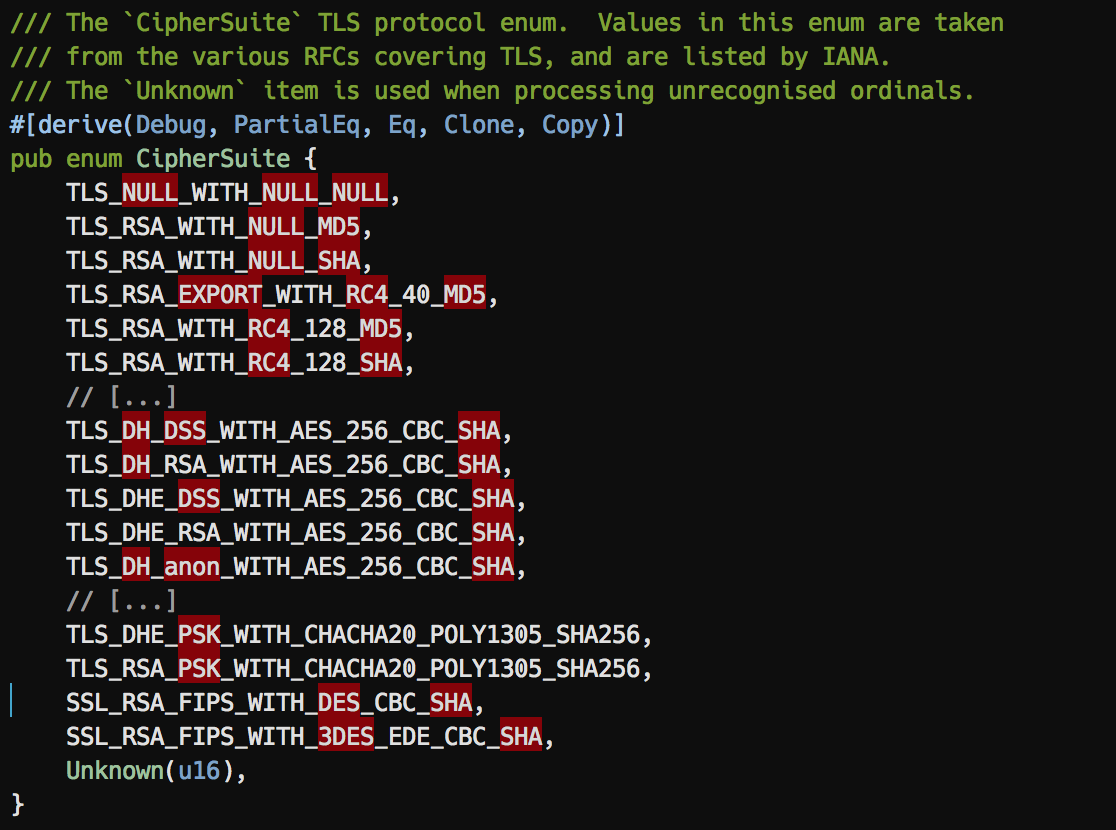
sslsecure.vim - Highlight insecure SSL/TLS cipher suites and protocols as errors in your editor
When configuring or programming SSL/TLS servers, at some point a SSL/TLS cipher suite and a list of supported protocols have to be chosen. Unfortunately, not all configuration options are safe. :(
Meet sslsecure.vim! A plugin for the Vim editor, that marks insecure SSL/TLS cipher suites and protocols as errors. See all potentially insecure options right in your editor!
Features
- Mark insecure SSL ciphers as errors
- Mark insecure SSL protocols as errors
- Works with all configuration files (web servers, mail servers, …)
- Works with all source code (independently on the used programming language)
- Works on top of regular syntax highlighting
Encryption works. Properly implemented strong crypto systems are one of the few things that you can rely on.
– Edward Snowden
Screenshots
Enough words, see sslsecure.vim in action!
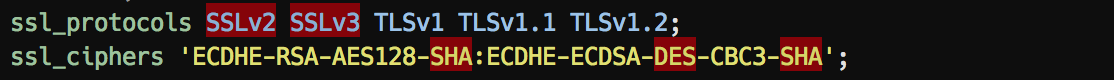
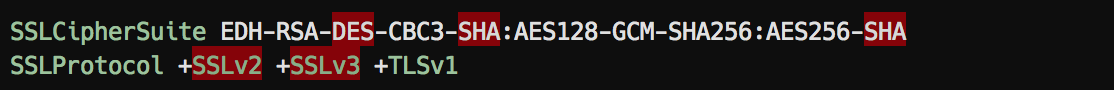
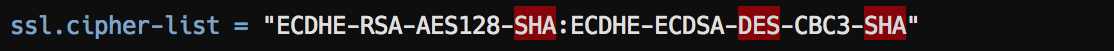
Web Servers
Nginx:
Apache:
Lighttpd:
Mail Servers
Postix:
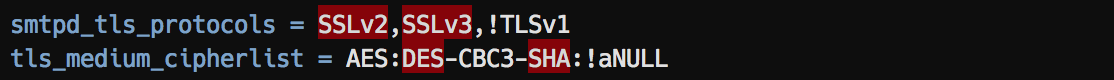
Exim:
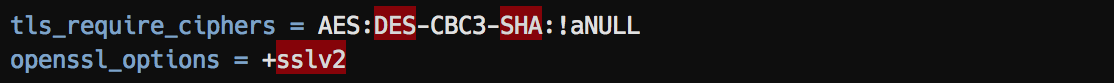
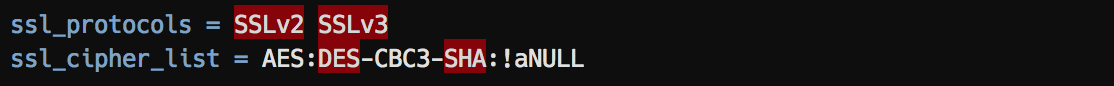
Dovecot:
Load Balancers
Haproxy:
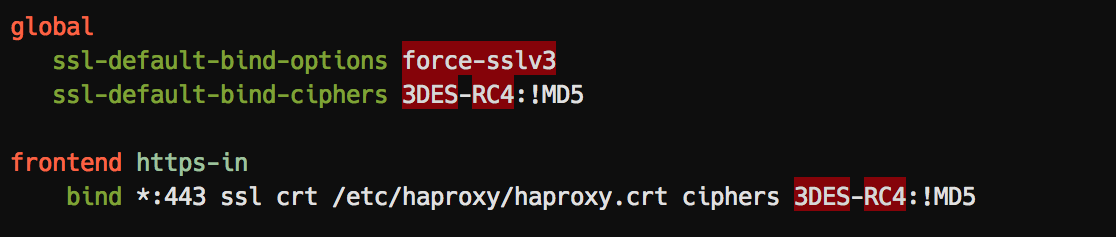
FTP Servers
ProFTPd:
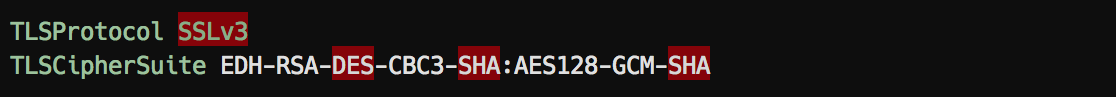
Databases
PostgreSQL:

MariaDB/ MySQL
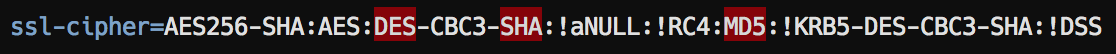
Programming languages
C (OpenSSL):
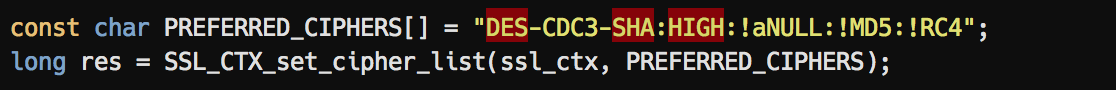
Go:
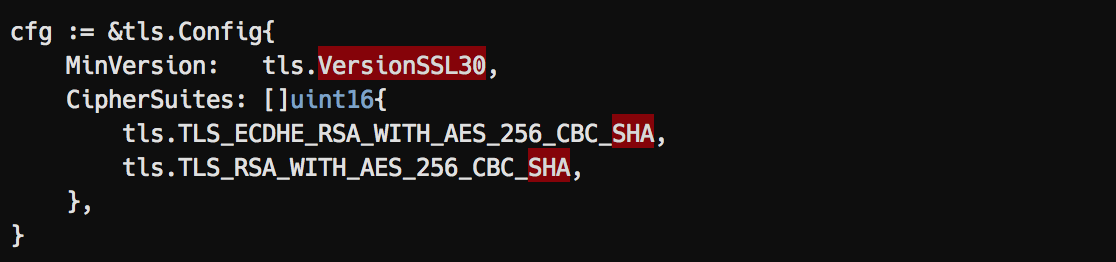
Jana:
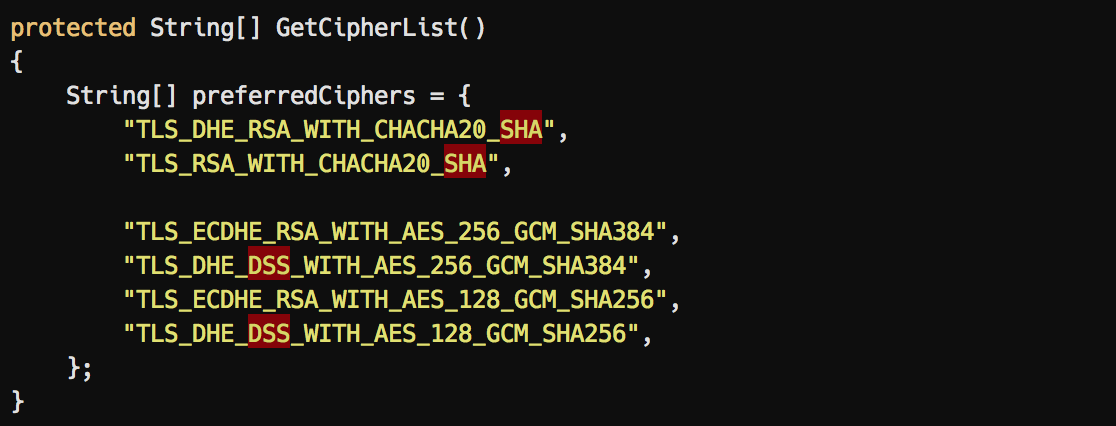
Additional notes on runtime cipher expanding
Cipher suites are expanded upon runtime. This is especially important when using +CHIPER statements in your suite, as insecure ciphers might be included upon runtime.
Example: The following (suggested by Cipherli.st) cipher suite doesn’t seem to contain any insecure ciphers when specifying:
EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:AES256+EDH
However, depending on your OpenSSL/ LibreSSL version, this suite expands upon runtime to the following (note the insecure DSS and SHA ciphers!):
$ openssl chipers 'EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:AES256+EDH' | vim
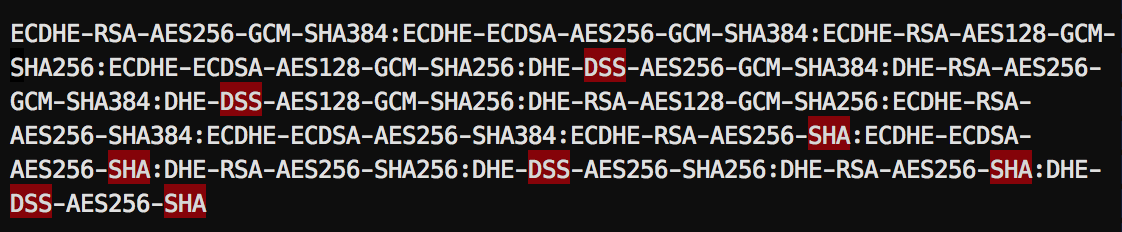
The plugin currently doesn’t save you from this pitfall. It’s therefore recommended, not to use the + statement in your cipher suite.
There’s an issue that discusses whether this plugin should also highlight all + statements.
Feedback
I’m neither a mathematician, nor a cryptographer. If you are one and you have feedback to this plugin, find a flaw, please open an issue or contact me.
Installation
Just plug it into your favorite Vim package manager:
" Plug
Plug 'chr4/sslsecure.vim
" Dein.vim
call dein#add('chr4/sslsecure.vim')
" Vundle
Plugin 'chr4/sslsecure.vim'
Using sslsecure.vim and nginx.vim together
sslsecure.vim was inspired by my other plugin
nginx.vim, which also automatically tries to detect insecure settings, but is nginx specific. Both plugins can be used alongside - nginx.vim automatically detects when sslsecure.vim is installed, so errors are not highlighted twice.
Edit: Gracias a Redeszone por un revisión muy bien sobre esta extensión!
Edit: Christian Rebischke packaged this plugin for Archlinux users in the Archlinux User Repository (AUR)
Edit: Auch ein Danke an Heise für den Artikel über dieses Plugin!